European Vulnerability Database (EUVD) Launch: Strategic Briefing
The European Union Agency for Cybersecurity (ENISA) has officially launched the European Vulnerability Database (EUVD), representing a significant shift in the global vulnerability management landscape. This system offers both strategic opportunities and implementation challenges for organisations. Key takeaway: Don't view it as "yet another system to monitor" but as a strategic redundancy that strengthens your security posture while aligning with EU regulatory requirements.
Why This Matters Now
On 13 May 2025, ENISA officially launched the European Vulnerability Database (EUVD), a significant development in the EU's cybersecurity infrastructure. This system, mandated by the NIS2 Directive, represents Europe's move toward greater technological sovereignty in vulnerability management whilst maintaining coordination with existing global systems.
The timing couldn't be more critical. Just last month, the U.S. government nearly discontinued funding for MITRE's Common Vulnerabilities and Exposures (CVE) programme—a cornerstone of global vulnerability tracking for 25 years—before CISA intervened with last-minute emergency funding for 11 months. This near-miss exposed a dangerous dependency on single-nation infrastructure for critical cybersecurity functions.
ENISA began developing the EUVD in June 2024 and has been operating a limited-access beta version since early 2025. The system is now fully operational and publicly accessible.
What Technical Leaders Need to Know
The Architecture: More Than Just Another Database
The EUVD isn't merely duplicating existing systems but offers enhanced functionality through:
Specialised dashboard views for critical vulnerabilities, actively exploited vulnerabilities, and EU-coordinated vulnerabilities
Multi-source intelligence aggregation from open-source databases, national CSIRTs, vendor advisories, and exploitation data
Near real-time updates rather than the delayed processing that has plagued other vulnerability databases
Machine-readable security advisories through Common Security Advisory Framework (CSAF) support
Identification and Interoperability: Playing Nice with Others
The EUVD employs its own identification format (EUVD-year-designation) whilst maintaining interoperability with existing systems through:
Cross-referencing with CVE IDs
Supporting multiple vulnerability tracking systems
Integration with open-source correlation tools
Compatibility with global security standards
This hybrid approach demonstrates the EU's commitment to both sovereignty and collaboration—creating independence without isolation.
Strategic Implications for Your Organisation
1. Sovereignty and Resilience
The EUVD represents a strategic move toward European digital sovereignty. By establishing a complementary vulnerability tracking system, the EU reduces dependency on U.S.-controlled infrastructure whilst maintaining compatibility with global standards.
For multinational organisations, this signals a need to develop regionally-aware security strategies that acknowledge the growing diversification of cybersecurity infrastructure.
2. Operational Redundancy
The near-collapse of CVE funding demonstrated the risk of single-point failures in critical cybersecurity infrastructure. The EUVD provides valuable redundancy, ensuring continuity even if disruptions occur elsewhere.
This is particularly significant for organisations operating in regulated EU sectors where continuous vulnerability awareness is not just good practice but a compliance requirement.
3. Regulatory Alignment
The EUVD is directly connected to the EU's regulatory framework, specifically the NIS2 Directive and the Cyber Resilience Act (CRA). Organisations operating in EU jurisdictions should view EUVD integration as a component of regulatory compliance strategy, particularly those in critical infrastructure sectors.
Strengths vs Challenges: A Balanced Assessment
What Works Well
Real-time updates: Unlike the U.S. National Vulnerability Database (NVD), which has experienced submission backlogs, the EUVD aims to provide near real-time updates
Enhanced visualisation: Prioritisation of critical and exploited vulnerabilities with improved interfaces
EU-specific focus: Special attention to vulnerabilities affecting European critical infrastructure
Multinational sponsorship: Reduced political volatility compared to single-nation funded alternatives
Implementation Hurdles
Maturity: As a new system, the EUVD will require time to reach full operational effectiveness
Integration complexity: Organisations will need to incorporate another vulnerability tracking system into existing security operations
Potential divergence: Despite commitment to interoperability, regional differences in vulnerability classification could emerge over time
Implementation Roadmap: From Strategy to Action
First 90 Days
Establish EUVD monitoring: Configure vulnerability management platforms to incorporate EUVD data feeds alongside existing CVE monitoring
Update security policies: Revise vulnerability management documentation to reference EUVD identifiers
Vendor assessment: Evaluate how security vendors and partners plan to integrate EUVD into their workflows
Medium-term Strategy (3-12 months)
Automation integration: Develop workflows that incorporate EUVD data for vulnerability prioritisation, particularly for EU-based assets
Training and awareness: Educate security teams on EUVD's structure and capabilities
Feedback participation: Contribute to ENISA's EUVD feedback programme to shape the platform's development
Long-term Positioning (12+ months)
Regional risk assessment: Develop region-specific vulnerability management approaches
Regulatory alignment: Position vulnerability management practices within the broader context of evolving EU cybersecurity regulations
Resilience planning: Design processes that remain effective regardless of potential disruptions to any single vulnerability tracking system
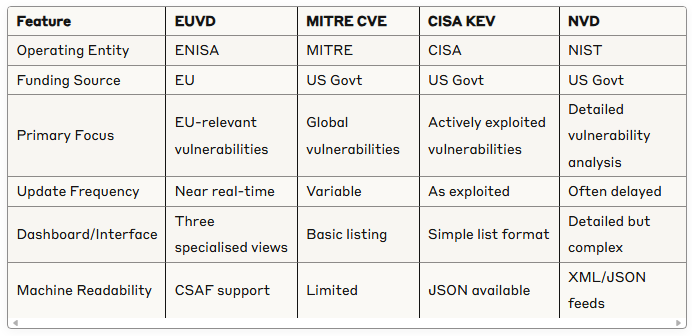
How EUVD Compares to Existing Systems
The Balanced Approach Forward
The European Vulnerability Database represents both a strategic opportunity and an operational challenge. While adding complexity to vulnerability management processes, it provides valuable redundancy and potentially enhanced visibility into critical vulnerabilities, particularly those affecting European assets.
The most prudent approach is neither over-reliance on EUVD nor dismissal of its significance, but rather thoughtful integration into existing security operations. Organisations should position themselves to benefit from multiple, complementary sources of vulnerability intelligence while maintaining efficiency in remediation workflows.
ENISA has explicitly stated that 2025 will be dedicated to further improving the EUVD based on stakeholder feedback. Technical decision makers should actively participate in this process to ensure the system evolves to meet organisational needs.